guide to hack mifare classic card First Key Recovery. CRYPTO-1 uses two 48 bits-long keys on Mifare Classic cards to encrypt the data on its sectors. Each key can be configured to be used for reading or writing on a sector..
Make sure that NFC is enabled on the device and that it has an NFC tag nearby. Run the app and bring the NFC tag close to the device. You should see a toast message with the tag ID displayed .
0 · MIFARE ultralight vs classic
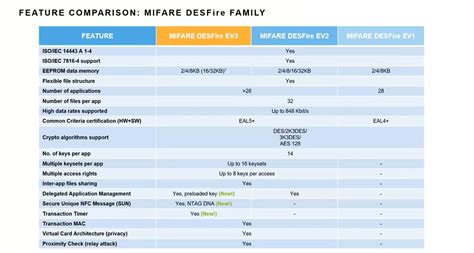
1 · MIFARE classic vs desfire
2 · MIFARE classic download
3 · MIFARE classic card recovery tool
4 · MIFARE classic card format
5 · MIFARE classic 1k cards
6 · MIFARE classic 1k card specification
7 · MIFARE 1k vs 4k
iOS 15 and NFC Issues (Not a Support Request) iOS. Just tried running an automation from an .
There’s plenty of guides online on how to crack the private keys that are supposed to make the card secure. Conveniently, [Guillermo] had a reader/writer on hand for these very cards.. The first attack on Mifare cards is called Darkside attack, which exploit the weak pseudo-random generator on the card to discover a single .How to Crack Mifare 1k RFID card. The NFC tag I analyzed is a so called “Mifare Classic 1k” tag. 1k stands for the size of data the tag can store. There are also other types like the “Mifare Classic 4k” and the “Mifare Mini” each having a .The Mifare Cracking GUI (mcgui) identifies, cracks, and clones both original and hardened Mifare Classic cards. Mcgui provides a simple user interface for existing Mifare cracking functions. .
In order to make a perfect clone, you will need a magic card which allows you to overwrite the manufacture block. There is blog posts, youtube videos, with all needed information to get you . First Key Recovery. CRYPTO-1 uses two 48 bits-long keys on Mifare Classic cards to encrypt the data on its sectors. Each key can be configured to be used for reading or writing on a sector.. Mifare Classic EV1 („hardened”) The „nested” and „darkside” attacks exploit implementation flaws (PRNG, side channel, .). Mifare Classic EV1, Plus in Classic mode . In this post I will share how to clone a MiFare Classic card using the Proxmark 3 Easy. Requirements: Hardware . Proxmark3 Easy ; Software. The RRG / Iceman git repo .

Proxmark3 Mifare Classic 1k (Crack/Dump/Duplicate) The darkside attack (for weak mifare) can be processed with a low cost hardware like the ARC122U, with mfcuk/mfoc over the libnfc. .– The use of Mifare Classic Cards for any system gives the fake sensation of security because it’s cracked since 2007 and exists public exploits since 2009 that allows anyone to clone/copy those cards as demonstrated. – The unique effective solution is exchange all cards in circulation by more secure cards. (Ex: There’s plenty of guides online on how to crack the private keys that are supposed to make the card secure. Conveniently, [Guillermo] had a reader/writer on hand for these very cards.. The first attack on Mifare cards is called Darkside attack, which exploit the weak pseudo-random generator on the card to discover a single key. This attack aims to recover one key from the.
How to Crack Mifare 1k RFID card. The NFC tag I analyzed is a so called “Mifare Classic 1k” tag. 1k stands for the size of data the tag can store. There are also other types like the “Mifare Classic 4k” and the “Mifare Mini” each having a different memory size. A Mifare Classic 1k tag contains 16 sectors. Each of these sectors has 3 .The Mifare Cracking GUI (mcgui) identifies, cracks, and clones both original and hardened Mifare Classic cards. Mcgui provides a simple user interface for existing Mifare cracking functions. The available cracking options through mcgui are the Dark Side, Hard Nested, and Nested attacks.
In order to make a perfect clone, you will need a magic card which allows you to overwrite the manufacture block. There is blog posts, youtube videos, with all needed information to get you started. First Key Recovery. CRYPTO-1 uses two 48 bits-long keys on Mifare Classic cards to encrypt the data on its sectors. Each key can be configured to be used for reading or writing on a sector.. Mifare Classic EV1 („hardened”) The „nested” and „darkside” attacks exploit implementation flaws (PRNG, side channel, .). Mifare Classic EV1, Plus in Classic mode (SL1) – fixes the exploit vectors. Your example card „Mifare Classic EV1” with guest hotel card content. In this post I will share how to clone a MiFare Classic card using the Proxmark 3 Easy. Requirements: Hardware . Proxmark3 Easy ; Software. The RRG / Iceman git repo (found here: https://github.com/RfidResearchGroup/proxmark3) Process: Obtain keys. Default keys ; Non-default keys; Dump card content; Write dump to empty card; Obtains keys
Proxmark3 Mifare Classic 1k (Crack/Dump/Duplicate) The darkside attack (for weak mifare) can be processed with a low cost hardware like the ARC122U, with mfcuk/mfoc over the libnfc. Nowadays, this attack is not covering a lot of Mifare classic card anymore.– The use of Mifare Classic Cards for any system gives the fake sensation of security because it’s cracked since 2007 and exists public exploits since 2009 that allows anyone to clone/copy those cards as demonstrated. – The unique effective solution is exchange all cards in circulation by more secure cards. (Ex: There’s plenty of guides online on how to crack the private keys that are supposed to make the card secure. Conveniently, [Guillermo] had a reader/writer on hand for these very cards..
The first attack on Mifare cards is called Darkside attack, which exploit the weak pseudo-random generator on the card to discover a single key. This attack aims to recover one key from the.How to Crack Mifare 1k RFID card. The NFC tag I analyzed is a so called “Mifare Classic 1k” tag. 1k stands for the size of data the tag can store. There are also other types like the “Mifare Classic 4k” and the “Mifare Mini” each having a different memory size. A Mifare Classic 1k tag contains 16 sectors. Each of these sectors has 3 .The Mifare Cracking GUI (mcgui) identifies, cracks, and clones both original and hardened Mifare Classic cards. Mcgui provides a simple user interface for existing Mifare cracking functions. The available cracking options through mcgui are the Dark Side, Hard Nested, and Nested attacks.
In order to make a perfect clone, you will need a magic card which allows you to overwrite the manufacture block. There is blog posts, youtube videos, with all needed information to get you started. First Key Recovery. CRYPTO-1 uses two 48 bits-long keys on Mifare Classic cards to encrypt the data on its sectors. Each key can be configured to be used for reading or writing on a sector.. Mifare Classic EV1 („hardened”) The „nested” and „darkside” attacks exploit implementation flaws (PRNG, side channel, .). Mifare Classic EV1, Plus in Classic mode (SL1) – fixes the exploit vectors. Your example card „Mifare Classic EV1” with guest hotel card content. In this post I will share how to clone a MiFare Classic card using the Proxmark 3 Easy. Requirements: Hardware . Proxmark3 Easy ; Software. The RRG / Iceman git repo (found here: https://github.com/RfidResearchGroup/proxmark3) Process: Obtain keys. Default keys ; Non-default keys; Dump card content; Write dump to empty card; Obtains keys
australian passport rfid protection
MIFARE ultralight vs classic
MIFARE classic vs desfire
MIFARE classic download
why-a-cloak-007 November 3, 2023, 4:45pm 1. I have coded a working .
guide to hack mifare classic card|MIFARE classic vs desfire