a privacy-preserving lightweight authentication protocol for low-cost rfid tags This paper introduces a lightweight authentication protocol for low-cost RFID tags . That’s because contactless credit card payments are enabled by a type of RFID technology called near-field communication, or NFC. When you wave your credit card or phone’s digital wallet in .Method 2: Looking for signs on the card: Some cards may have visible indications indicating the presence of RFID or NFC technology. Look for any logos or symbols on the card that suggest contactless communication. .
0 · A Privacy
1 · A Lightweight Authentication Protocol for Low
Most debit and credit cards these days already have an NFC tag built-in. The aforementioned apps simply emulate these tags, with permission from the issuing bank or financial institution.
This paper introduces a lightweight authentication protocol for low-cost RFID tags. Compared with previous work, our solution provides better traceability protection while keeping the system efficient in terms of computation and communication.This paper introduces a lightweight authentication protocol for low-cost RFID tags. Compared . This paper introduces a lightweight authentication protocol for low-cost RFID tags . To remove security vulnerabilities, we propose a robust mutual authentication .
In this paper, we analyze the security vulnerabilities of a lightweight .This paper introduces a lightweight authentication protocol for low-cost RFID tags. Compared with previous work, our solution provides better traceability protection while keeping the system efficient in terms of computation and communication.
This paper introduces a lightweight authentication protocol for low-cost RFID tags. Compared with previous work, our solution provides better traceabil-ity protection while keeping the system efficient in terms of computation and communication. Our scheme also maintains comparable strength regarding other security aspects. I. INTRODUCTION. This paper introduces a lightweight authentication protocol for low-cost RFID tags that provides better traceability protection while keeping the system efficient in terms of computation and communication and maintains comparable .
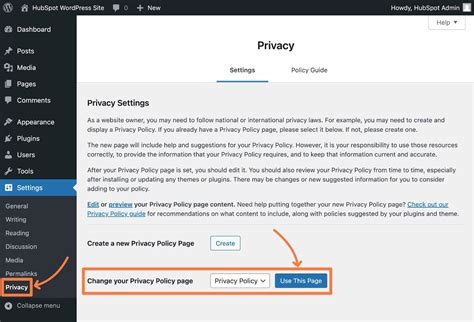
To remove security vulnerabilities, we propose a robust mutual authentication protocol between a tag and a back-end server for low-cost RFID system that guarantees data privacy and location.In this paper, we analyze the security vulnerabilities of a lightweight authentication protocol recently proposed by Li et al. (2006), and then propose a new lightweight protocol to improve the security and to reduce the computational cost for identifying a tag from O(n) to O(1).In this paper, a privacy preserving authentication protocol for RFID that relies on a single cryptographic component, a lightweight stream cipher, is constructed.
In this paper we propose a novel privacy-preserving mutual authentication protocol for RFID systems using the recently proposed ultra-lightweight cryptographic algorithm Hummingbird-2. The new protocol is resistant to the most common attacks against the .Our experimental results demonstrate that the Hummingbird-2 mutual authentication protocol provides a highly effective and efficient security and privacy solution for low-cost passive RFID tags. On the other hand, with the rapid deployment of RFID in a multitude fields, its security and privacy issues have also emerged. The authors of [] pointed out that due to low computational capabilities, the chip-less sensory tags were unable to adopt mature and complex encryption mechanisms to protect themselves. Consequently, low-cost RFID tags are currently .
The most recent ultra-lightweight mutual authentication protocol (UMAP) adopts a mechanism for key updating to keep the security forward and backward. The back-end server updates the secret keys immediately after sending the final message.This paper introduces a lightweight authentication protocol for low-cost RFID tags. Compared with previous work, our solution provides better traceability protection while keeping the system efficient in terms of computation and communication.

This paper introduces a lightweight authentication protocol for low-cost RFID tags. Compared with previous work, our solution provides better traceabil-ity protection while keeping the system efficient in terms of computation and communication. Our scheme also maintains comparable strength regarding other security aspects. I. INTRODUCTION.
This paper introduces a lightweight authentication protocol for low-cost RFID tags that provides better traceability protection while keeping the system efficient in terms of computation and communication and maintains comparable . To remove security vulnerabilities, we propose a robust mutual authentication protocol between a tag and a back-end server for low-cost RFID system that guarantees data privacy and location.In this paper, we analyze the security vulnerabilities of a lightweight authentication protocol recently proposed by Li et al. (2006), and then propose a new lightweight protocol to improve the security and to reduce the computational cost for identifying a tag from O(n) to O(1).
A Privacy
In this paper, a privacy preserving authentication protocol for RFID that relies on a single cryptographic component, a lightweight stream cipher, is constructed.
In this paper we propose a novel privacy-preserving mutual authentication protocol for RFID systems using the recently proposed ultra-lightweight cryptographic algorithm Hummingbird-2. The new protocol is resistant to the most common attacks against the .Our experimental results demonstrate that the Hummingbird-2 mutual authentication protocol provides a highly effective and efficient security and privacy solution for low-cost passive RFID tags. On the other hand, with the rapid deployment of RFID in a multitude fields, its security and privacy issues have also emerged. The authors of [] pointed out that due to low computational capabilities, the chip-less sensory tags were unable to adopt mature and complex encryption mechanisms to protect themselves. Consequently, low-cost RFID tags are currently .
A Lightweight Authentication Protocol for Low
nope - Smartrip worked perfectly for me. In the wallet, search for a transport pass, search for Washington; add a smartrip card. Add funds (You'll need an internet connection at .
a privacy-preserving lightweight authentication protocol for low-cost rfid tags|A Lightweight Authentication Protocol for Low