methods to secure the rfid tags There are several techniques commonly used by attackers to exploit RFID vulnerabilities. One such method is known as RFID cloning, where an attacker copies the information from a legitimate tag onto a counterfeit tag. By doing so, the attacker can gain unauthorized access to restricted areas or deceive systems that rely on RFID authentication. Smartphones that have IR blasters are pretty rare so even if you did emulate it with an NFC .All prices are the current market price. NFC Reader (Nintendo 3DS | Video Games) prices are based on the historic sales. The prices shown are calculated using our proprietary algorithm. Historic sales data are completed sales with a buyer and a seller .
0 · what rfid tag will do
1 · rfid tags for home use
2 · rfid radio frequency identification tags
3 · rfid is involved when using
4 · rfid for dummies
5 · rfid cards for beginners
6 · radio frequency identification tags are
7 · example of rfid tags
Information. NFC Tools GUI is a cross Platform software : it works on Mac, Windows and Linux. You can read and write your NFC chips with a simple and lightweight user interface. Connect your NFC reader to your computer like the .
One of the easiest ways to prevent RFID hacking is to invest in badges and wallets that block RFID signals. RFID blockers prevent both scanners and legitimate readers from scanning your card so using it off-premises is the .There are several techniques commonly used by attackers to exploit RFID vulnerabilities. One such method is known as RFID cloning, where an attacker copies the information from a legitimate tag onto a counterfeit tag. By doing . Two common methods of this are skimming and eavesdropping: 1. Skimming: To skim is to surreptitiously read a tag, often through the use of a handheld reader. If your system is configured according to a widely used protocol, it may be at risk of being skimmed. 2. One of the easiest ways to prevent RFID hacking is to invest in badges and wallets that block RFID signals. RFID blockers prevent both scanners and legitimate readers from scanning your card so using it off-premises is the perfect way .
There are several techniques commonly used by attackers to exploit RFID vulnerabilities. One such method is known as RFID cloning, where an attacker copies the information from a legitimate tag onto a counterfeit tag. By doing so, the attacker can gain unauthorized access to restricted areas or deceive systems that rely on RFID authentication.
In general, metal and water are the best ways to block radio signals to and from your RFID chip. Once you block this signal, the RFID tag is unreadable. Equip Your Wallet and Pockets to Stop RFID Signals The new standard will secure passive tags, such as those exploited by RFDump and found in most supply chain applications, with “a secured forward link.” “When data is written to the tag, the. Overview. Introduction to RFID and its applications. Types of security attacks to Passive RFID Tags. Impersonation. Information Leakage. Physical Manipulation. Types of Protection Methods for RFID Tags. PUFs and Unclonable RFID Tags. Other means of security.
A secure solution is to combine RFID tags with AlpVision’s Fingerprint technology. Fingerprint is a patent technology that leverages the specific characteristics of the product surface to authenticate it.
This post aims to highlight several important RFID related security issues. RFID Counterfeiting: depending on the computing power, RFID can be classified into three categories: Basic tags; Tags that uses symmetric keys; Tags that uses public-key; Since basic tags do not use any encryption, they can be counterfeited easily. This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks.Secure your RFID system with our top 5 essential tips! From requiring physical inputs to data encryption, enhance your security against cyber threats. Two common methods of this are skimming and eavesdropping: 1. Skimming: To skim is to surreptitiously read a tag, often through the use of a handheld reader. If your system is configured according to a widely used protocol, it may be at risk of being skimmed. 2.
One of the easiest ways to prevent RFID hacking is to invest in badges and wallets that block RFID signals. RFID blockers prevent both scanners and legitimate readers from scanning your card so using it off-premises is the perfect way .There are several techniques commonly used by attackers to exploit RFID vulnerabilities. One such method is known as RFID cloning, where an attacker copies the information from a legitimate tag onto a counterfeit tag. By doing so, the attacker can gain unauthorized access to restricted areas or deceive systems that rely on RFID authentication. In general, metal and water are the best ways to block radio signals to and from your RFID chip. Once you block this signal, the RFID tag is unreadable. Equip Your Wallet and Pockets to Stop RFID Signals The new standard will secure passive tags, such as those exploited by RFDump and found in most supply chain applications, with “a secured forward link.” “When data is written to the tag, the.
Overview. Introduction to RFID and its applications. Types of security attacks to Passive RFID Tags. Impersonation. Information Leakage. Physical Manipulation. Types of Protection Methods for RFID Tags. PUFs and Unclonable RFID Tags. Other means of security.
what rfid tag will do
rfid tags for home use


A secure solution is to combine RFID tags with AlpVision’s Fingerprint technology. Fingerprint is a patent technology that leverages the specific characteristics of the product surface to authenticate it.
This post aims to highlight several important RFID related security issues. RFID Counterfeiting: depending on the computing power, RFID can be classified into three categories: Basic tags; Tags that uses symmetric keys; Tags that uses public-key; Since basic tags do not use any encryption, they can be counterfeited easily.
This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks.
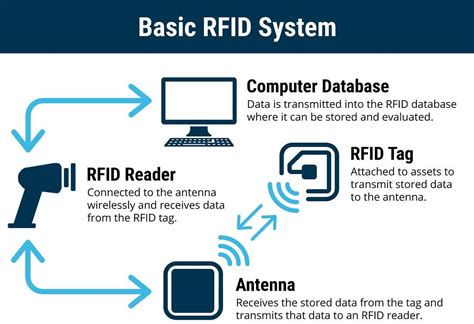
rfid radio frequency identification tags
rfid is involved when using
Step 2: Tap New Automation or + (from the top-right corner). Step 3: Here, scroll down or search for NFC. Tap it. Step 4: Tap Scan. Hold your device over an NFC tag/sticker. Step 5: Name the tag .
methods to secure the rfid tags|radio frequency identification tags are