biometric authentication vs smart cards Biometric authentication is a security process that compares a person’s characteristics to a stored set of biometric data in order to grant access to buildings, applications, systems, and more.
Click LOAD TAG to load Amiibo data of the villager you want.; Click SAVE TAG to save chosen Amiibo data on to the tag of your choice. *Be aware that the NFC tags are NOT re-writable in this case, as official Nintendo Amiibos also lock in .
0 · what is biometric authentication
1 · types of biometric identification
2 · pros and cons of biometrics
3 · okta biometric authentication
4 · mfa vs biometrics
5 · is biometric authentication expensive
6 · examples of biometric authentication
7 · are biometrics real
Part 3: Ink Errors. Ink errors are the misprints that happen during ink application (aka printing) and are easily the most common type of misprint. MTG cards are printed via a mass production process known as offset lithographic printing. .
Hoping for a passwordless future? Multifactor authentication using biometrics may be the answer. Consider the pros, cons and implications of biometric authentication before deploying.Using smart cards with biometrics results in a trusted credential for authenticating an . Hoping for a passwordless future? Multifactor authentication using biometrics may be the answer. Consider the pros, cons and implications of biometric authentication before deploying.Using smart cards with biometrics results in a trusted credential for authenticating an individual’s identity using one-to-one biometric verification. With the biometric template stored on the smart card, comparison can be made locally, without the need for .
In this article we explore how smart cards and biometrics can work together for enhanced security, privacy and performance. Security requirements. Smart cards are both secure and portable. Additionally, they can securely store data.Biometric authentication is a security process that compares a person’s characteristics to a stored set of biometric data in order to grant access to buildings, applications, systems, and more. Biometric authentication is defined as a security measure that matches the biometric features of a user looking to access a device or a system. Access to the system is granted only when the parameters match those stored in the database for that particular user. In this article, we will explain the difference between FIDO2 and smartcard authentication and discuss the benefits and potential drawbacks of each. Difference between Passwordless Authentication Methods: FIDO2, SmartCard, Passwordless Phone Auth - YouTube. Difference between Passwordless Authentication Methods: FIDO2, SmartCard, Passwordless .
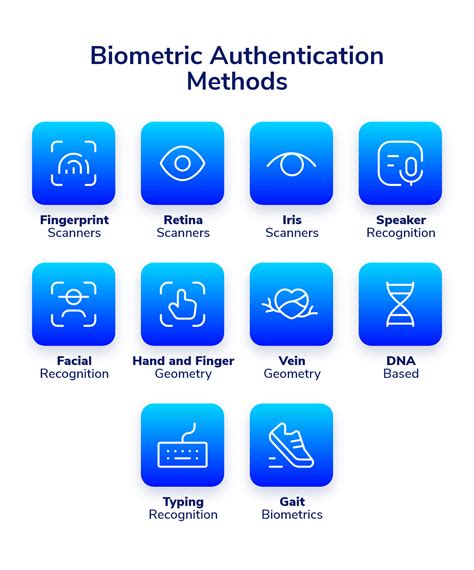
This is done for the purpose of performing trusted communications between parties for computing and telecommunications applications. In this paper, we differentiate between machine-by-ma-chine authentication (or simply machine authentication) and human-by-machine authentication (user authentication) (see Fig. 1). Something you have (Keyfob token, key, debit card, smartcard, mobile phone); or Something you are (biometric data, such as fingerprint, retina, iris, face, veins, DNA, voiceprint, hand, typical usage patterns)
what is biometric authentication
This chapter discusses the technologies of biometrics and (RFID-enabled) smart cards and their use in electronic passports, and reflects on the introduction of e-passports, and the surrounding issues regarding security and the shift in the balance of power between citizen and government. Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications. Hoping for a passwordless future? Multifactor authentication using biometrics may be the answer. Consider the pros, cons and implications of biometric authentication before deploying.Using smart cards with biometrics results in a trusted credential for authenticating an individual’s identity using one-to-one biometric verification. With the biometric template stored on the smart card, comparison can be made locally, without the need for .
In this article we explore how smart cards and biometrics can work together for enhanced security, privacy and performance. Security requirements. Smart cards are both secure and portable. Additionally, they can securely store data.Biometric authentication is a security process that compares a person’s characteristics to a stored set of biometric data in order to grant access to buildings, applications, systems, and more.
Biometric authentication is defined as a security measure that matches the biometric features of a user looking to access a device or a system. Access to the system is granted only when the parameters match those stored in the database for that particular user. In this article, we will explain the difference between FIDO2 and smartcard authentication and discuss the benefits and potential drawbacks of each. Difference between Passwordless Authentication Methods: FIDO2, SmartCard, Passwordless Phone Auth - YouTube. Difference between Passwordless Authentication Methods: FIDO2, SmartCard, Passwordless .This is done for the purpose of performing trusted communications between parties for computing and telecommunications applications. In this paper, we differentiate between machine-by-ma-chine authentication (or simply machine authentication) and human-by-machine authentication (user authentication) (see Fig. 1).
Something you have (Keyfob token, key, debit card, smartcard, mobile phone); or Something you are (biometric data, such as fingerprint, retina, iris, face, veins, DNA, voiceprint, hand, typical usage patterns) This chapter discusses the technologies of biometrics and (RFID-enabled) smart cards and their use in electronic passports, and reflects on the introduction of e-passports, and the surrounding issues regarding security and the shift in the balance of power between citizen and government.
types of biometric identification

pros and cons of biometrics
okta biometric authentication
If I could clone the tag to my phone and emulate that chip it was save me small minutes getting in and out of work. it doesn't work that way since they (NFC against HID Proximity) work in different frequencies. Apple's (and other .
biometric authentication vs smart cards|examples of biometric authentication